DefectDojo supports Single Sign-On (SSO) using OpenID Connect (OIDC). This guide shows how to securely integrate DefectDojo with Keycloak, making sure the OIDC token includes the correct aud (audience) claim so DefectDojo accepts the authentication.
If you’ve followed my previous posts, you already have:
- DefectDojo installed with Docker and HAProxy on Ubuntu 24.04
- Keycloak installed with MariaDB and NGINX reverse proxy
This post connects the two to enable secure OIDC-based login.
Prerequisites
- Working DefectDojo and Keycloak setup with valid HTTPS
- Realm name:
maksonlee.com - Admin access to both systems
- Create a Client in Keycloak
In the Keycloak Admin Console (https://keycloak.maksonlee.com), go to Clients → Create client, use the following values:
| Field | Value |
|---|---|
| Client ID | defectdojo |
| Client Protocol | openid-connect |
| Access Type | confidential |
| Standard Flow Enabled | checked |
| Valid Redirect URIs | https://defectdojo.maksonlee.com/complete/keycloak/ |
| Base URL | https://defectdojo.maksonlee.com/ |
| Web Origins | + or leave blank |
- Create a Client Scope for the
audClaim
Go to Client Scopes → Create client scope, fill in:
| Field | Value |
|---|---|
| Name | dojo-audience-scope |
| Protocol | openid-connect |
| Type | Optional |
Click Save.
Then go to the Mappers tab for this scope and click Add mapper and By configuration
| Field | Value |
|---|---|
| Name | aud |
| Mapper Type | Audience |
| Included Client Audience | defectdojo |
| Add to ID Token | checked |
| Add to Access Token | checked |
| Add to Token Introspection | checked |
Save the mapper.
- Attach the Scope to the DefectDojo Client
- Go to Clients → defectdojo → Client Scopes
- Click Add client scope
- Select
dojo-audience-scope - Click Add as default
Now all tokens issued for this client will include "aud": ["defectdojo"].
- Configure DefectDojo for OIDC
In docker-compose.override.yml, configure:
uwsgi:
environment:
# Security settings
DD_SESSION_COOKIE_SECURE: "true"
DD_CSRF_COOKIE_SECURE: "true"
DD_SECURE_SSL_REDIRECT: "true"
# Keycloak SSO integration
DD_SOCIAL_AUTH_KEYCLOAK_OAUTH2_ENABLED: "true"
DD_SOCIAL_AUTH_KEYCLOAK_KEY: "defectdojo" # client_id in Keycloak
DD_SOCIAL_AUTH_KEYCLOAK_SECRET: <client-secret>
DD_SOCIAL_AUTH_KEYCLOAK_PUBLIC_KEY: "MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAyyQTRT/wfBZHHAN82PQrR2uWzQs00CsECx0tVTi5UTnsRH2IA2j5qO1S+ARwdpk+WZSv7JKa8LvznCvYf6+2V2vI0eb56nxAGUKgd5DjWkG6qLa7LrN8CjGE4G7irc3DgIiuCUOVkMSjDlFKyiCjRQ+zHPIWEHJCpB9LQbOEx/oXOtgMq9cILPcYbEb3HAvGAO16L7zM0bz/egZJyz3pBLqrxNm3+AsONTKw26IRT3E/8Imli8mOsvTmoVa8fNKplcY2yi321Pi4QEGkP8a/xH//n1/Z7iI0r4uaFMqFw2zwd/h7TCjH4DKZgLgcvOFrM5VzRLohZ9IlDX7uhX/ImwIDAQAB"
DD_SOCIAL_AUTH_KEYCLOAK_AUTHORIZATION_URL: "https://keycloak.maksonlee.com/realms/maksonlee.com/protocol/openid-connect/auth"
DD_SOCIAL_AUTH_KEYCLOAK_ACCESS_TOKEN_URL: "https://keycloak.maksonlee.com/realms/maksonlee.com/protocol/openid-connect/token"Make sure your DefectDojo instance is restarted after applying these changes.
- Disable Profile Editing (Optional but Recommended)
If Keycloak manages user identity, users should not edit their profile in DefectDojo.
- Go to
https://defectdojo.maksonlee.com/system_settings - Find Enable user profile for writing
- Uncheck it
- Click Submit
This disables the profile edit view for all users.
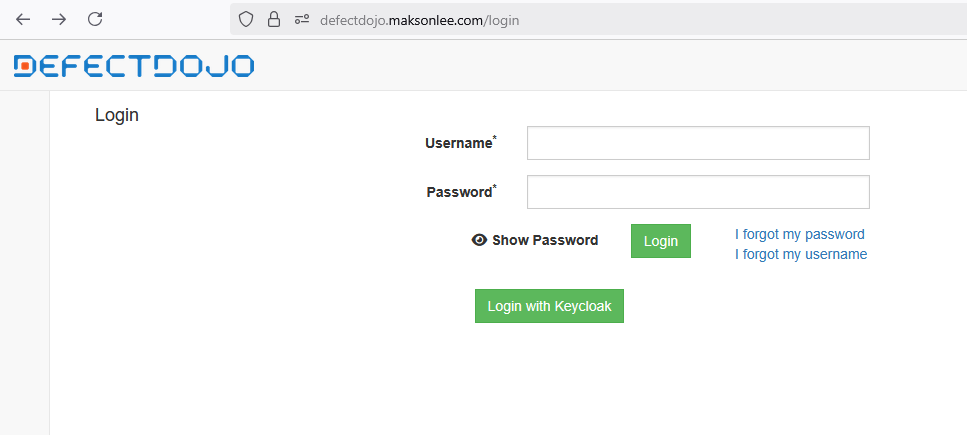
- Test the Login
Visit:
https://defectdojo.maksonlee.com/login
If DD_SOCIAL_LOGIN_AUTO_REDIRECT=True, you’ll be redirected directly to:
https://defectdojo.maksonlee.com/login/keycloak
Otherwise, you’ll see a login screen with a green Login with Keycloak button:
Did this guide save you time?
Support this site