Architecture Overview:
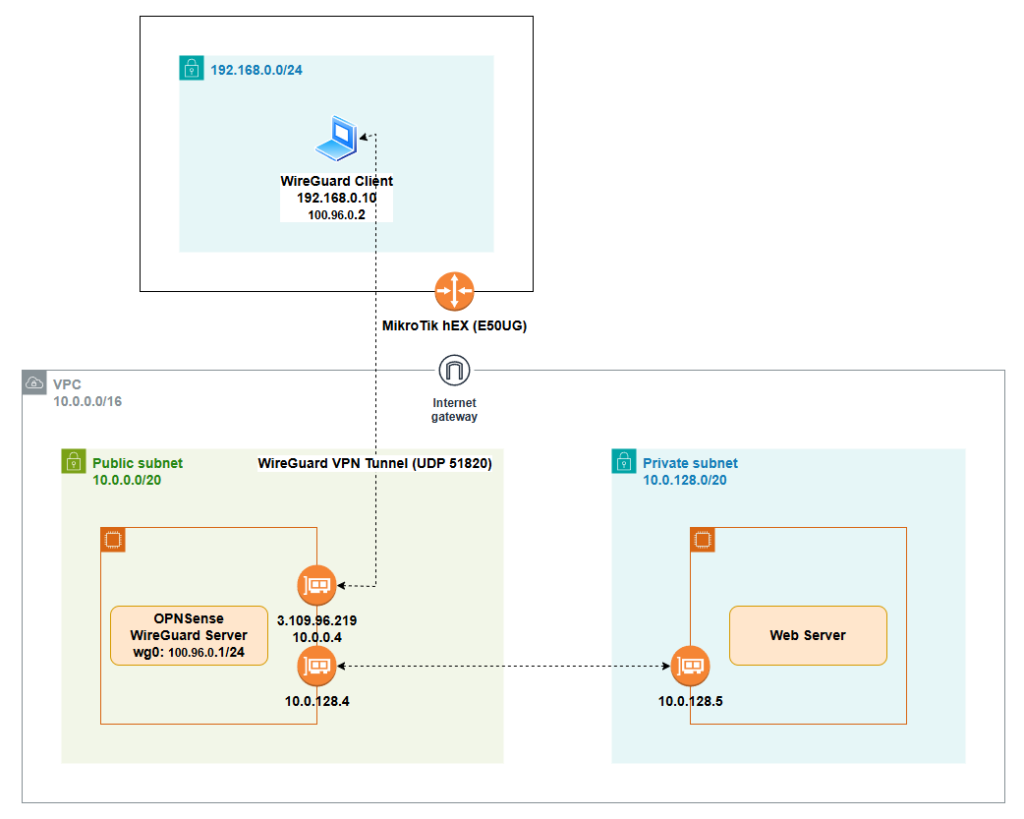
This setup runs WireGuard on an AWS EC2-based OPNsense firewall (WireGuard server) in the public subnet (10.0.0.0/20). The server has a public endpoint (3.109.96.219:51820/UDP) and a WireGuard tunnel network (wg0: 100.96.0.1/24).
From the homelab side, a WireGuard client (LAN 192.168.0.10, tunnel IP 100.96.0.2) connects to the OPNsense server through the Internet (behind a MikroTik hEX router). Once the tunnel is up, the client can reach selected AWS networks defined by AllowedIPs, including the AWS private subnet (10.0.128.0/20) where the internal web server (10.0.128.5) lives.
In short:
- OPNsense (AWS) = WireGuard Server / VPN Gateway
- Homelab PC = WireGuard Client
- AllowedIPs controls which AWS subnets are reachable over the tunnel
PART 1 — Set Up WireGuard on OPNsense
- Enable WireGuard Globally
- Go to VPN → WireGuard → Instances
- Scroll to the bottom
- Check Enable WireGuard
- Click Apply
- Create the WireGuard Instance
- Go to VPN → WireGuard → Instances
- Click Add
- Fill in:
Name:wg0
Listen Port:51820
Tunnel Address:100.96.0.1/24 - Click Generate new keypair
- Click Save
- Assign & Enable the Interface
- Go to Interfaces → Assignments
- In + Assign a new interface
Fill in:
Device: wg0
Description: WG_VPN - Click Add
- Go to Interfaces → WG_VPN
- Check Enable Interface
- Save & Apply
- Add Firewall Rules
- Go to Firewall → Rules → WG_VPN
- Click Add
- Fill in:
Source:100.96.0.0/24
Destination: any
Action: Pass
Description: Allow VPN client traffic
Save & Apply - Go to Firewall → Rules → WAN
- Click Add
- Fill in:
Protocol: UDP
Port:51820
Action: Pass
Description: Allow WireGuard
Save & Apply
PART 2 — Generate Client Key Pair & Config (Using OPNsense Peer Generator)
- Use Peer Generator to Create Client Key + Config
- Go to VPN → WireGuard → Peer Generator
- Fill in:
Instance: wg0
Name: windows-client
IP Address: 100.96.0.2/32
Allowed IPs: 100.96.0.1/32 (the WireGuard interface on OPNsense), 10.0.128.0/20 (my AWS private subnet), 10.0.0.0/20 (my AWS public subnet)
DNS Servers: 100.96.0.1
Keepalive Interval: 25 (keeps the tunnel alive by sending periodic packets) - Copy the config, you will use it later
- Click Store and Generate Next
PART 3 — Use the Config on Your Client
On Windows
- Install WireGuard from https://www.wireguard.com/install
- Click Add Tunnel → Add empty tunnel and then paste the config you copied in step 5
- Save
Did this guide save you time?
Support this site