In our previous post, we installed Ceph Squid v19 with RGW S3 and the Ceph Dashboard on three Ubuntu 24.04 bare-metal nodes. RGW runs on port 8081, and the Dashboard runs on port 8080 with SSL disabled.
In this follow-up, we’ll add HAProxy in front of both services, with:
- SSL termination using Let’s Encrypt (DNS challenge)
- Load balancing across RGW nodes
- Dashboard access over HTTPS (on port
8443) - S3 API exposed via HTTPS (on port
443) - Automatic certificate renewal
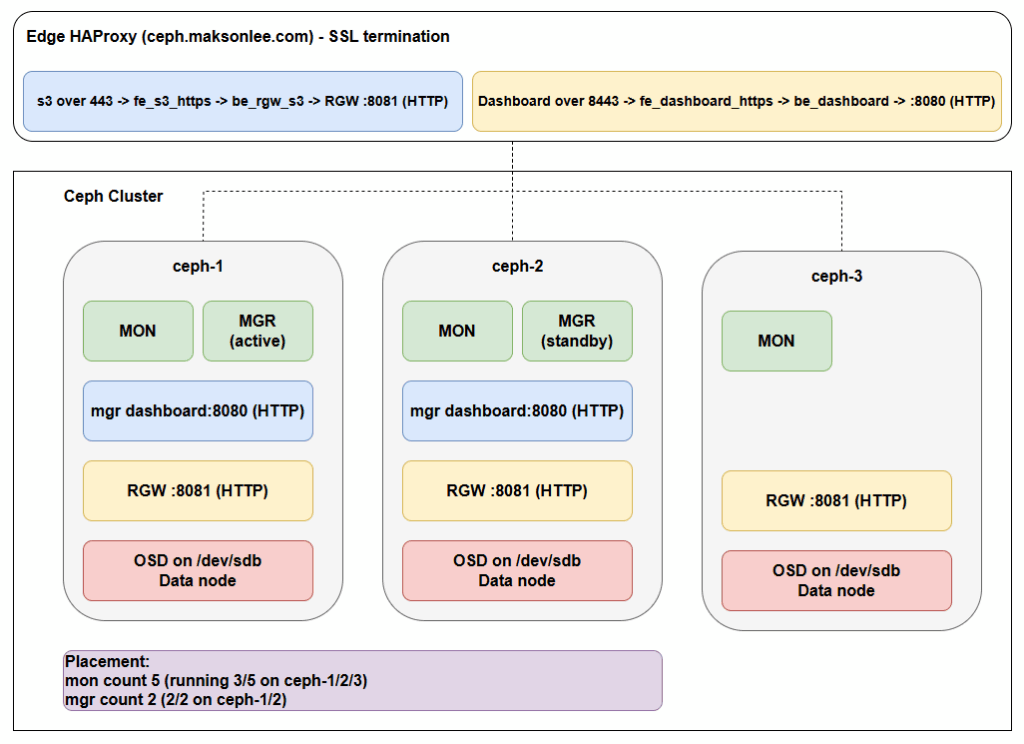
Cluster Topology
| Hostname | IP Address | Role |
|---|---|---|
| ceph.maksonlee.com | 192.168.0.81 | HAProxy + SSL termination |
| ceph-1.maksonlee.com | 192.168.0.82 | MON, MGR, RGW (8081), Dashboard (8080) |
| ceph-2.maksonlee.com | 192.168.0.83 | MON, MGR, RGW (8081) Dashboard (8080) |
| ceph-3.maksonlee.com | 192.168.0.84 | MON, RGW (8081) |
- Install HAProxy 3.2 from PPA
sudo add-apt-repository ppa:vbernat/haproxy-3.2 -y
sudo apt update
sudo apt install -y haproxy=3.2.*
sudo systemctl enable --now haproxy- Install Certbot with DNS Plugin
sudo apt install -y certbot python3-certbot-dns-cloudflare
mkdir -p ~/.secrets/certbot
vi ~/.secrets/certbot/cloudflare.inidns_cloudflare_api_token = YOUR_CLOUDFLARE_API_TOKENchmod 600 ~/.secrets/certbot/cloudflare.ini- Request SSL Certificate
sudo certbot certonly \
--dns-cloudflare \
--dns-cloudflare-credentials ~/.secrets/certbot/cloudflare.ini \
-d ceph.maksonlee.com- Bundle Certificate for HAProxy
sudo mkdir -p /etc/haproxy/certs/
sudo bash -c "cat /etc/letsencrypt/live/ceph.maksonlee.com/fullchain.pem \
/etc/letsencrypt/live/ceph.maksonlee.com/privkey.pem \
> /etc/haproxy/certs/ceph.maksonlee.com.pem"
sudo chmod 600 /etc/haproxy/certs/ceph.maksonlee.com.pem- Configure HAProxy (443 → RGW, 8443 → Dashboard)
Edit /etc/haproxy/haproxy.cfg:
# S3 over 443
frontend fe_s3_https
bind *:443 ssl crt /etc/haproxy/certs/ceph.maksonlee.com.pem
mode http
default_backend be_rgw_s3
# Dashboard over 8443
frontend fe_dashboard_https
bind *:8443 ssl crt /etc/haproxy/certs/ceph.maksonlee.com.pem
mode http
default_backend be_dashboard
backend be_rgw_s3
mode http
balance roundrobin
server rgw1 192.168.0.82:8081 check
server rgw2 192.168.0.83:8081 check
server rgw3 192.168.0.84:8081 check
backend be_dashboard
mode http
balance roundrobin
server ceph1 192.168.0.82:8080 check
server ceph2 192.168.0.83:8080 checkReload HAProxy:
sudo systemctl restart haproxy- Automate Certificate Renewal
Create deploy hook to reload HAProxy on renewal:
sudo tee /etc/letsencrypt/renewal-hooks/deploy/reload-haproxy.sh > /dev/null <<EOF
#!/bin/bash
cat /etc/letsencrypt/live/ceph.maksonlee.com/fullchain.pem \
/etc/letsencrypt/live/ceph.maksonlee.com/privkey.pem \
> /etc/haproxy/certs/ceph.maksonlee.com.pem
systemctl reload haproxy
EOF
sudo chmod +x /etc/letsencrypt/renewal-hooks/deploy/reload-haproxy.shFinal Test
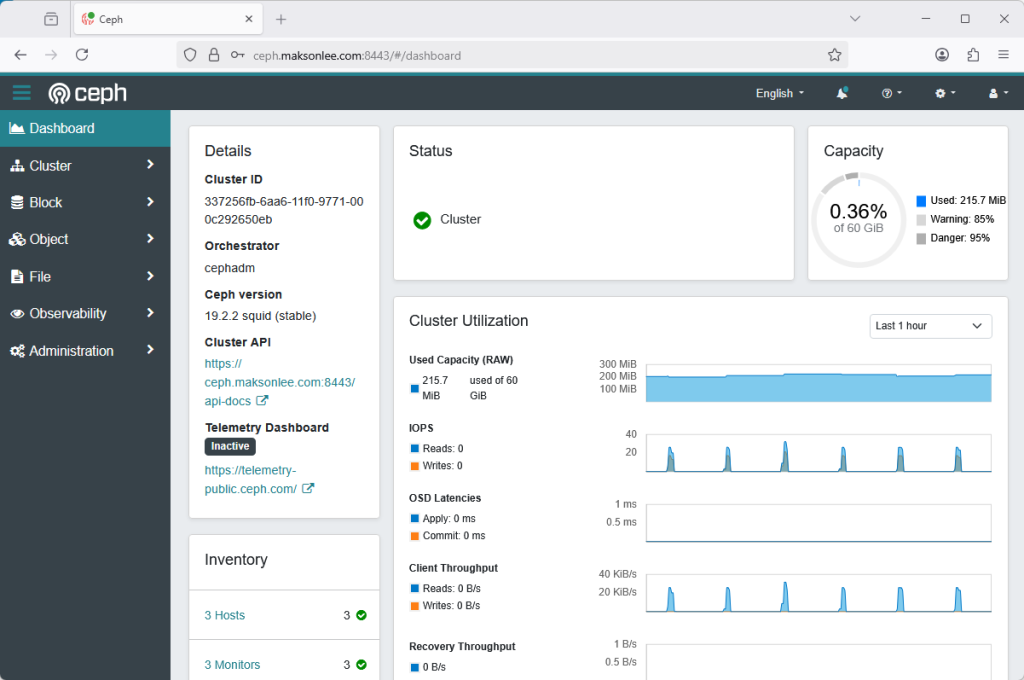
Access Ceph Dashboard
https://ceph.maksonlee.com:8443
Access Ceph S3 API (via AWS CLI)
s3cmd --configure
s3cmd --dump-config | grep host_host_base = ceph.maksonlee.com:443
host_bucket = ceph.maksonlee.coms3cmd ls2025-07-27 08:40 s3://testbucketWith HAProxy handling SSL, routing, and load balancing, your Ceph RGW and Dashboard setup is now scalable and production-ready, with secure HTTPS access and seamless certificate automation.
Did this guide save you time?
Support this site