By default, Jenkins allows all logged-in users full access, convenient for testing, but dangerous for real teams. Even matrix-based security becomes hard to manage as your team grows.
The cleaner, scalable alternative is the Role-Based Authorization Strategy plugin, which lets you define Global Roles like admin, developer, or viewer and map users or groups to them.
In this post, I’ll walk you through setting up secure Jenkins access using only Global Roles, ideal for most environments, especially when combined with Keycloak group-based SSO.
- Install the Role-Based Authorization Strategy Plugin
- Go to Manage Jenkins → Plugins → Available
- Search for
Role-based Authorization Strategy - Click Install
- Restart Jenkins after installation
- Enable Role-Based Strategy
- Navigate to Manage Jenkins → Security
- Under Authorization, choose Role-Based Strategy
- Click Save
This unlocks a new menu:
Manage Jenkins → Manage and Assign Roles
- Define Global Roles
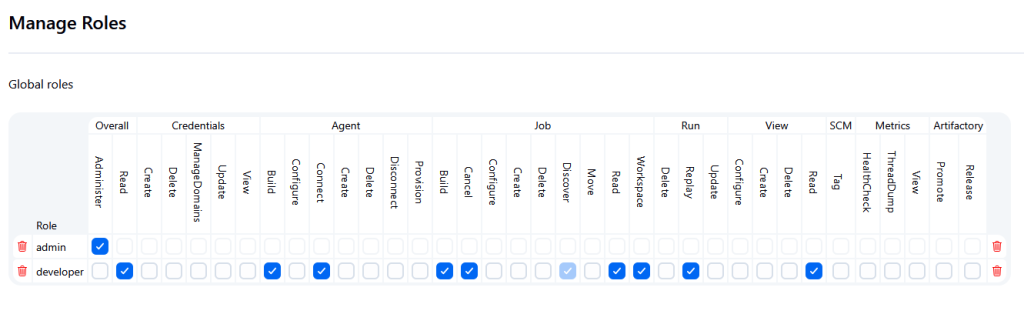
Go to Manage and Assign Roles → Manage Roles
Create roles like:
admin: full Jenkins controldeveloper:software developers who can trigger builds, replay them, and view logs, but cannot modify jobs
Recommended developer permissions:
| Category | Permissions |
|---|---|
| Overall | Read |
| Job | Read, Build, Cancel, Discover |
| Run | Replay |
| Agent | Build |
| View | Read |
- Assign Roles to Users or Groups
Go to Manage and Assign Roles → Assign Roles
Here’s what it might look like:
In our setup:
| Group from Keycloak | Assigned Jenkins Role |
|---|---|
jenkins-admin (Keycloak) | admin |
jenkins-developer (Keycloak) | developer |
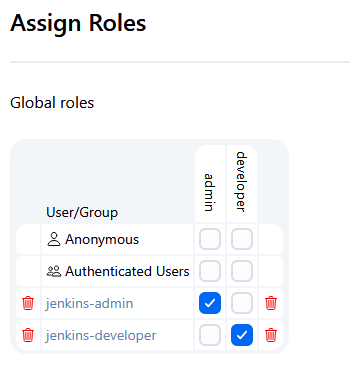
These groups are mapped from Keycloak client roles using the method described here.
About the “Restrict Project Naming” Warning
After enabling the plugin, Jenkins may display this:
“The Restrict project naming configuration is not set to the Role-based Strategy…”
Should you act?
No, not in this setup.
This only applies if you’re using Item Roles with job name patterns (e.g., ^team-a-.*).
You’re using only Global Roles, so you can safely dismiss the warning.
Did this guide save you time?
Support this site